MAC Address: 00:1C:DF:58:9D:0A (Belkin International) Nmap done: 1 IP address (1 host up) scanned in 139.26 seconds Nmap includes an advanced option, “-top-ports”, which can be used to test.
Zenmap is the official Nmap Security Scanner GUI. It is a multi-platform (Linux, Windows, Mac OS X, BSD, etc.) free and open source application which aims to make Nmap easy for beginners to use while providing advanced features for experienced Nmap users. Frequently used scans can be saved as profiles to make them easy to run repeatedly. When I need to locate the IPs of devices by their mac address on a Windows system, I normally use Advanced IP Scanner (from radmin.com) to scan the network, then I use arp -a to list the mac addresses. Is it possible to use nmap to perform the same function in Linux and possibly in Windows? Can nmap to the scanning and produce both IPs and MAC. Zenmap is an free and open source GUI designed to be used with nmap.Zenmap is multiplatform tool which supports Linux, Ubuntu, Mint, Kali, Fedora, CentOS., Windows, Mac OS X, BSD etc. Nmap is very powerful tool for network scanning and vulnerability discovery but it is completely command line based.Zenmap can be used by novice users to scan network and discover vulnerabilities.
- 1987 次查看 314 次下载
- 分类:工具
- 标签:zenmaps zenmap guis gui frontends frontend viewers viewer nmaps nmap nmaps nmap utility explorations exploration auditings auditing zenmaps zenmap multis multus platforms platform graphicals graphical frontends frontend vie
- 时间:2019年02月19日 更新 文件大小: 32.1 MB
- 开发商:Gordon Lyon 官网首页
- 支持类型: Mac OS X 10.9 or later
- 支持语言:未知
来自Mac App Store官方介绍
Zenmap is a GUI frontend and results viewer for Nmap.
Nmap is a free and open source utility for network exploration and security auditing. Zenmap is a multi-platform X Window System graphical frontend and results viewer for Nmap. Ncat is a general-purpose network sending and receiving utility, a reimplementation of Netcat. Ndiff is a an Nmap scan comparison utility. Nping is a tool for packet generation and sending.
This package contains Nmap, Zenmap, Ncat, Ndiff, and Nping. It is intended to work on Intel and PowerPC Macs running Mac OS X 10.4.11 or later

Installation of all packages is optional. Unselect Zenmap to get just the command-line tool. Unselect Nmap if you prefer to use a copy of Nmap that is already installed. Zenmap will not work without Nmap.
The nmap, ncat, ndiff, and nping command-line binaries will be installed in /usr/local/bin, and additional support files will be installed in /usr/local/share. The Zenmap application bundle will be installed in /Applications/Zenmap.app.
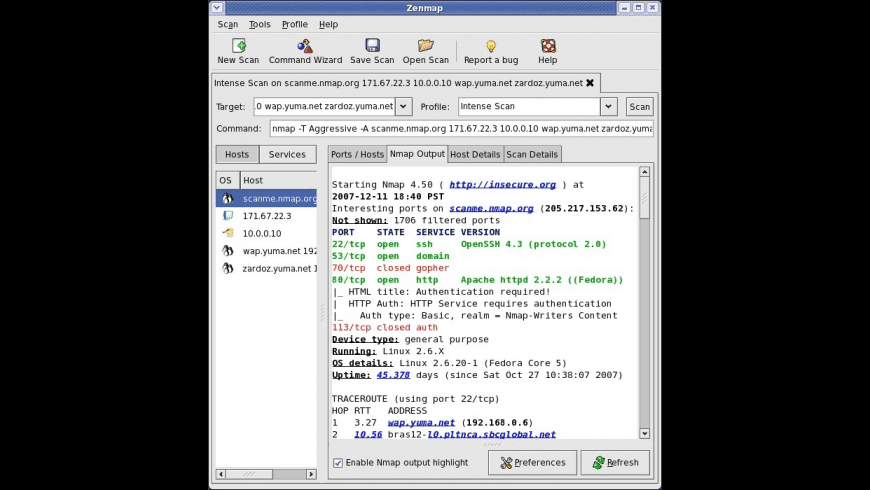
…更多…
v7.70版本新功能
Version 7.70:
Full release notes available here
Highlights:
- Integrated all of your service/version detection fingerprints submitted from March 2017 to August 2017 (728 of them). The signature count went up 1.02% to 11,672, including 26 new softmatches. We now detect 1224 protocols from filenet-pch, lscp, and netassistant to sharp-remote, urbackup, and watchguard. We will try to integrate the remaining submissions in the next release
- Integrated all of your IPv4 OS fingerprint submissions from September 2016 to August 2017 (667 of them). Added 298 fingerprints, bringing the new total to 5,652. Additions include iOS 11, macOS Sierra, Linux 4.14, Android 7, and more
- Integrated all 33 of your IPv6 OS fingerprint submissions from September 2016 to August 2017. New groups for OpenBSD 6.0 and FreeBSD 11.0 were added, as well as strengthened groups for Linux and OS X
- Added the --resolve-all option to resolve and scan all IP addresses of a host. This essentially replaces the resolveall NSE script
- [NSE][SECURITY] Nmap developer nnposter found a security flaw (directory traversal vulnerability) in the way the non-default http-fetch script sanitized URLs. If a user manualy ran this NSE script against a malicious web server, the server could potentially (depending on NSE arguments used) cause files to be saved outside the intended destination directory. Existing files couldn't be overwritten. We fixed http-fetch, audited our other scripts to ensure they didn't make this mistake, and updated the httpspider library API to protect against this by default
…更多…
相关截图 图片数: 1 张(点击图片查看大图)
- 上一条:ColorPickMe
- 下一条:Burmese Dictionary
下载列表 文件数: 2文件大小: 32.1 MB举报
| 文件名 | 版本 | 下载次数 | 上传时间 | 上传者 | 下载类型 | 操作 | |
|---|---|---|---|---|---|---|---|
| 0. | http://nmap.org/download.html#macosx官网下载 | 最新 | - | - | 官方 | Mac | 点击下载 |
| 1. | nmap.org官方原版 | v7.01 | 149 | 2016-02-23 | 网友共享 | Mac 版 | 点击下载 |
| 2. | nmap.org官方原版 | v7.70 | 165 | 2019-02-19 | 网友共享 | Mac 版 | 点击下载 |
| 苹果软件园为积极推动苹果电脑在国内的发展,倡导资源共享,软件汉化。所有下载链接均来自网友分享试用,请24小时内删除!希望大家有条件的积极支持正版. 如果你的网盘有这个App的资源,欢迎共享下载地址哦,只需要几秒钟哦有网盘资源的点击感谢分享下载地址 | |||||||
↑ 如果您觉得从我们的分享中得到了帮助,并且希望我们持续发展下去,求打赏(ღ♡‿♡ღ)~谢谢您的鼓励。 | |||||||
How would you communicate with a device when you don’t have the IP?
You might be in a situation where you don’t have the IP address of a device in a local network, but all you have is records of the MAC or hardware address.
Or your computer is unable to display its IP due to various reasons, and you are getting a “No Valid IP Address” error.
Finding the IP from a known MAC address should be the task of a ReverseARP application, the counterpart of ARP.
But RARP is an obsolete protocol with many disadvantages, so it was quickly replaced by other protocols like BOOTP and DHCP, which deal directly with IP addresses.
In this article, we’ll show you how to find IPs and device vendors using MAC addresses with different methods for free.
Understanding ARP
ARP (Address Resolution Protocol) is the protocol in charge of finding MAC addresses with IPs in local network segments.
It operates with frames on the data link layer.
As you might already know, devices in the data link layer depend on MAC addresses for their communication.
Their frames encapsulate packets that contain IP address information.
A device must know the destination MAC address to communicate locally through media types like Ethernet or Wifi, in layer 2 of the OSI model.
Understanding how ARP works can help you find IPs and MAC addresses quickly.
The following message flow diagram can help you understand the concept:
- The local computer sends a ping (ICMP echo request) to a destination IP address (remote computer) within the same segment. Unfortunately, the local computer does not know the MAC address… it only knows the IP address.
- The destination hardware address is unknown, so the ICMP echo request is put on hold. The local computer only knows its source/destination IP and its source MAC addresses. ARP uses two types of messages, ARP Request and Reply.
The local computer sends an ARP REQUEST message to find the owner of the IP address in question.
This message is sent to all devices within the same segment or LAN through a broadcast MAC (FF:FF:FF:FF:FF:FF) as the destination.
- Because the remote computer is part of the same network segment, it receives the broadcast message sent by the local computer. All other computers in the LAN also receive the broadcast but they know that the destination IP is not theirs, so they discard the packet. Only the remote computer with destination IP, responds to the ARP REQUEST with an ARP REPLY, which contains the target MAC address.
- The local computer receives the ARP REPLY with the MAC address. It then resumes the ICMP echo request, and finally, the remote computer responds with an ICMP echo reply.
Finding IPs with ARP
You can use ARP to obtain an IP from a known MAC address.
But first, it is important to update your local ARP table in order to get information from all devices in the network.
Send a ping (ICMP echo reply) to the entire LAN, to get all the MAC entries on the table.
To ping the entire LAN, you can send a broadcast to your network.
Open the Command Prompt in Windows or terminal in macOS and type.
ping 192.168.0.255
My subnet is 192.168.0.0/24 (mask of 255.255.255.0), so the broadcast address is 192.168.0.255 which can be calculated or found with a “Print Route” command in Windows or a “netstat -nr” in macOS. Or can also be obtained with a subnet calculator.
For Windows:
Step 1.
- Open the CMD (Command Prompt)
- Go to the “Start” menu and select “Run” or press (Windows key + R) to open the Run application
- In the “Open” textbox type “cmd” and press “Ok”.
This will open the command-line interface in Windows.
Step 2.
- Enter the “arp” command.
- The arp command without any additional arguments will give you a list of options that you can use.
Step 3.
- Use the arp with additional arguments to find the IP within the same network segment.
- With the command “arp -a” you can see the ARP table and its entries recently populated by your computer with the broadcast ping.
Step 4.
- Reading the output.
- The information displayed in the arp-a is basically the ARP table on your computer.
- It shows a list with IP addresses, their corresponding physical address (or MAC), and the type of allocation (dynamic or static).
Let’s say you have the MAC address 60-30-d4-76-b8-c8 (which is a macOS device) and you want to know the IP.
From the results shown above, you can map the MAC address to the IP address in the same line.
The IP Address is 192.168.0.102 (which is in the same network segment) belongs to 60-30-d4-76-b8-c8.
You can forget about those 224.0.0.x and 239.0.0.x addresses, as they are multicast IPs.
For macOS:
Step 1:
- Open the Terminal App. go to Applications > Utilities > Terminal or Launchpad > Other > Terminal.
Step 2:
- Enter the “arp” command with an “-a” flag.
- Once you enter the command “arp -a” you’ll receive a list with all ARP entries to the ARP Table in your computer.
- The output will show a line with the IP address followed by the MAC address, the interface, and the allocation type (dynamic/static).
Finding IPs with the DHCP Server
The Dynamic Host Configuration Protocol (DHCP) is the network protocol used by TCP/IP to dynamically allocate IP addresses and other characteristics to devices in a network.
Download Zenmap For Mac
The DHCP works with a client/server mode.
The DHCP server is the device in charge of assigning IP addresses in a network, and the client is usually your computer.
For home networks or LANs, the DHCP Server is typically a router or gateway.
If you have access to the DHCP Server, you can view all relationships with IPs, MACs, interfaces, name of the device, and lease time in your LAN.
Step 1.
- Log into the DHCP Server. In this example, the DHCP server is the home gateway.
- If you don’t know the IP address of your DHCP Server/ Gateway, you can run an ipconfig (in Windows) or ifconfig (in macOS/Linux).
- This particular DHCP Server/Gateway has a web interface.
Step 2.
- Enter the IP address on the search bar of the web browser, and input the right credentials.
Step 3.
- Find the DHCP Clients List.
- In this TP-Link router, the DHCP Server functionality comes as an additional feature.
- Go to DHCP > DHCP Clients List. From this list, you can see the mapping between MAC addresses and their assigned IPs.
Using Sniffers
If you couldn’t find the IP in the ARP list or unfortunately don’t have access to the DHCP Server, as a last resort, you can use a sniffer.
Packet sniffers or network analyzers like Nmap (or Zenmap which is the GUI version) are designed for network security.

They can help identify attacks and vulnerabilities in the network.
With Nmap, you can actively scan your entire network and find IPs, ports, protocols, MACs, etc.
If you are trying to find the IP from a known MAC with a sniffer like Nmap, look for the MAC address within the scan results.
How to find the Device and IP with a Sniffer?
Step 1.
- Keep records of your network IP address information.
- In this case, my network IP is 192.168.0.0/24. If you don’t know it, a quick “ipconfig” in Windows cmd or an “ifconfig” in macOS or Linux terminal can show you the local IP and mask.
- If you can’t subnet, go online to a subnet calculator and find your network IP.
Step 2.
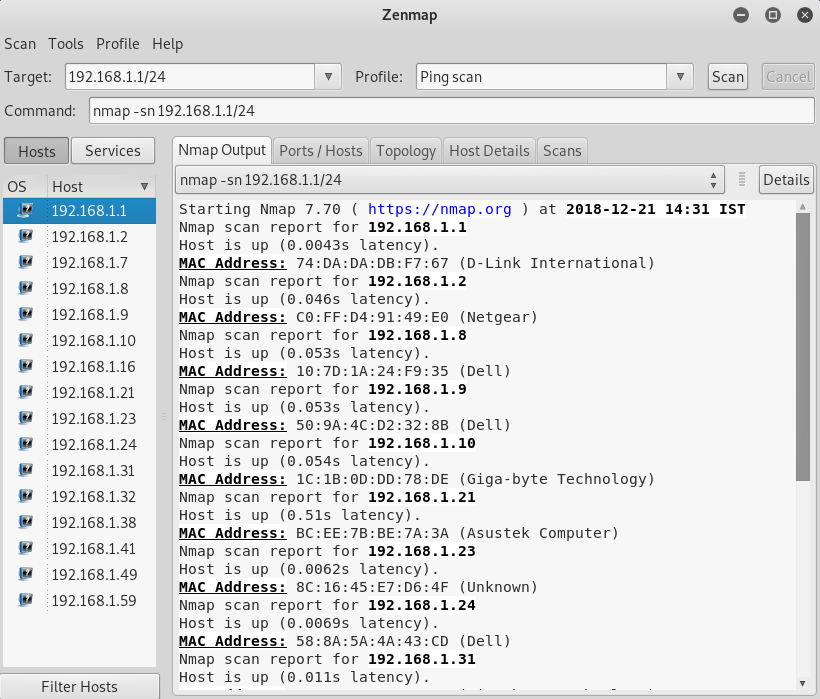
- Download and open Nmap.
- Download Nmap from this official link https://nmap.org/download.html and follow its straightforward installation process.
Step 3.
- Open Nmap (or Zenmap) and use the command “sudo nmap -sn (network IP)” to scan the entire network (without port scan).
- The command will list machines that respond to the Ping and will include their MAC address along with the vendor.
- Don’t forget the “sudo” command.
- Without it, you will not see MAC addresses.
Finding out the device vendor from a MAC address
Ok, so now you were able to find out the IP address using “arp -a” command or through the DHCP Server.
But what if you want to know more details about that particular device?
What vendor is it?
Your network segment or LAN might be full of different devices, from computers, firewalls, routers, mobiles, printers, TVs, etc.
And MAC addresses contain key information for knowing more details about each network device.
First, it is essential to understand the format of the MAC address.
Traditional MAC addresses are 48 bits represented in 12-digit hexadecimal numbers (or six octets).
The first half of the six octets represent the Organizational Unique Identifier (OUI) and the other half is the Network Interface Controller (NIC) which is unique for every device in the world.
There is not much we can do about the NIC, other than communicating with it.
But the OUI can give us useful information about the vendor if you didn’t use Nmap, which can also give you the hardware vendor.

A free online OUI lookup tool like Wireshark OUI Lookup can help you with this.
Zenmap For Mac Download
Just enter the MAC address on the OUI search, and the tool will look at the first three octets and correlate with its manufacturing database.
Final Words
Although the RARP (the counterpart of ARP) was specifically designed to find IPs from MAC addresses, it was quickly discontinued because it had many drawbacks.
RARP was quickly replaced by DHCP and BOOTP.
But ARP is still one of the core functions of the IP layer in the TCP/IP protocol stack.
It finds MAC addresses from known IPs, which is most common in today’s communications.
ARP works under the hood to keep a frequently used list of MACs and IPs.
But you can also use it to see the current mappings with the command arp -a.
Zenmap Windows 10
Aside from ARP, you can also use DHCP to view IP information. DHCP Servers are usually in charge of IP assignments.
If you have access to the DHCP server, go into the DHCP Client list and identify the IP with the MAC address.
Finally, you can use a network sniffer like Nmap, scan your entire network, and find IPs, and MACs.
Nmap Mac 64 Bit
If you only want to know the vendor, an online OUI lookup like Wireshark can help you find it quickly.
