The Terminal in macOS is one handy tool that few people make use of. Here we will show you how you can use the Terminal in macOS to scan your local network for troubleshooting, maintenance and general curiosity. It works a little differently from Linux’s utilities, with different flags in some cases, so don’t assume Linux skills will be accurate on macOS.
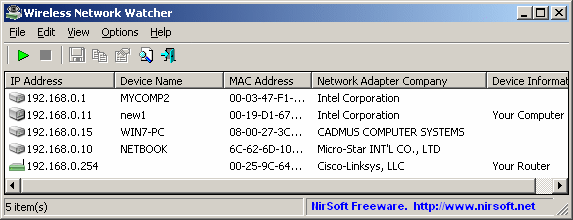
Who Is On My Wifi can monitor the LAN network which is being used by your PC, provides the details of all the devices using your LAN IP addresses and also provides desktop and sound notification whenever a new device is connected to the LAN network. The detail of a device includes their MAC address, IP address, PC name and connection status. It also has an automatic scan feature which scans.
Scan Your Local Network’s Open Ports with nmap
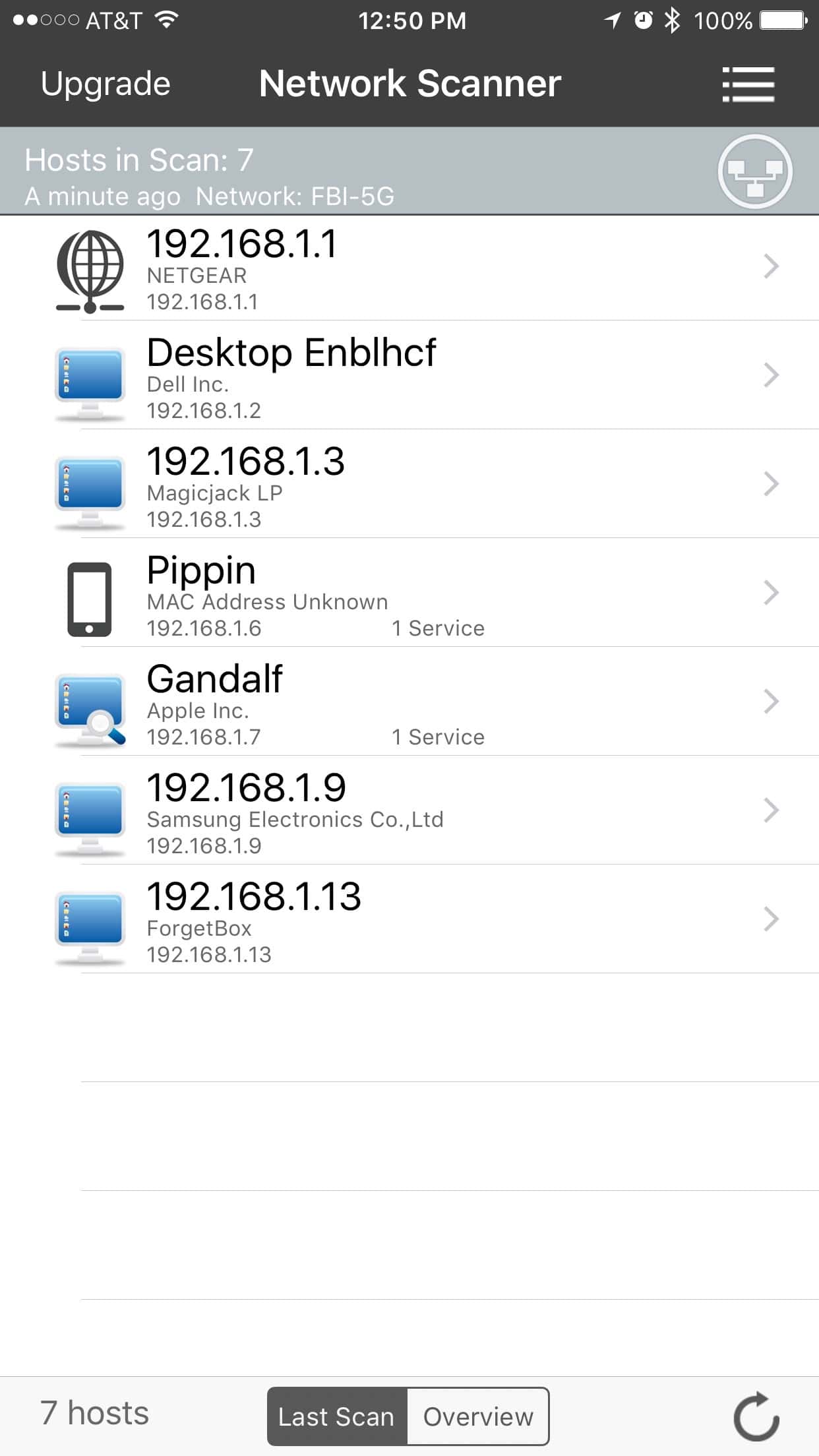
Scan Mac For Free
- IP Scanner is a cloud tool that scans your local network and returns a sortable list of the devices it discovers. Devices can be filtered, searched, and exported to CSV. By default, it detects and scans a local subnet, though you can also define a custom IP range.
- Ping Tester (Figure A) uses ICMP pings to detect devices on your network.
nmap is the king of command-line port scanners on macOS, but you’ll need to install it first.
Install nmap with Homebrew
If you have Homebrew installed, run
to download and install nmap and any necessary dependencies.
Scan with nmap
nmap is built to scan a provided hostname or network address and return a list of open ports. The name stands for “network mapper,” but it’s more of a port mapper.
The simplest way to run nmap is with an IP address or range of IP addresses specified as the target; replace with the appropriate IP address to scan on your local network. This specific command scans nmap’s educational testing server at scanme.org.
To scan for open ports on a range of IP addresses, use a slash.
To find the IP addresses of your router and various devices on your network, you can run arp or ipconfig.
Using the -A flag will force nmap to scan more aggressively, returning significantly more information but transparently revealing your presence in the server logs. The -A flag must be run with sudo.
This scans the defined IP address for the operating system (-O). Again, it must be run with sudo.

If you want to run nmap a little more stealthily, use the -sS flag:
Scan Local Network For Devices
This has the effect of forcing “half-open” scanning. This sends a TCP SYN packet to check if the port is open, but does not respond with an ACK packet when receiving an affirmative response. As such, the remote server likely won’t log the scan.
The -sS flag and other scanning mode switches must be run with sudo. For example, the -sP mode switch will scan for IP addresses but not ports, functioning something like arp below. See the nmap man page for more scanning modes.
Scan Network For Connected Devices
To get more verbose results, add the -vv or -v3 tag. This will turn on more verbose logging levels, producing a more readable but longer standard output. Depending on what you’re looking for, these flags might help you find it.
Of course, you can always pipe the results of nmap into grep to search for specific results. If you wanted to check port 22 only, for example, you might run the command below:
This will return no lines if the port is not available and return the port’s status line if available.
Scan Your Local Network’s Active IP Addresses with arp
arp scans your local network for connected devices. Because arp is designed to create and modify address resolution protocols, it has limited tools available for scanning your network. But it ships on every Mac, and it’s a rapid way to get specific information.
To see a list of all responding devices currently connected to your network, open Terminal and run:
This returns a list of all devices connected to your network, reported by IP address and MAC address.
There isn’t much more to arp. You can run arp -a -i en0 to only get reports from your network interface en0, but that’s all.
Conclusion
The most powerful tool for scanning your local network on macOS is nmap. arp is also useful for running a ping sweep across the network. ipconfig can report results for a specific interface but is more useful for reporting interface information than scanning a network.